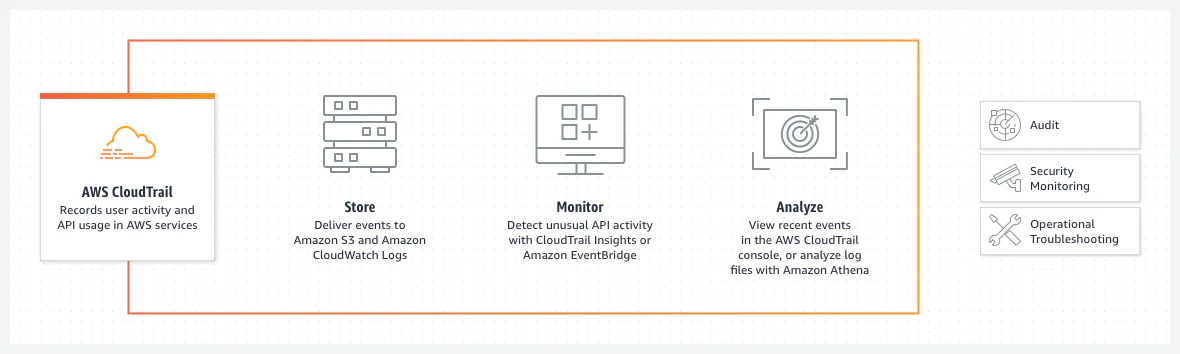
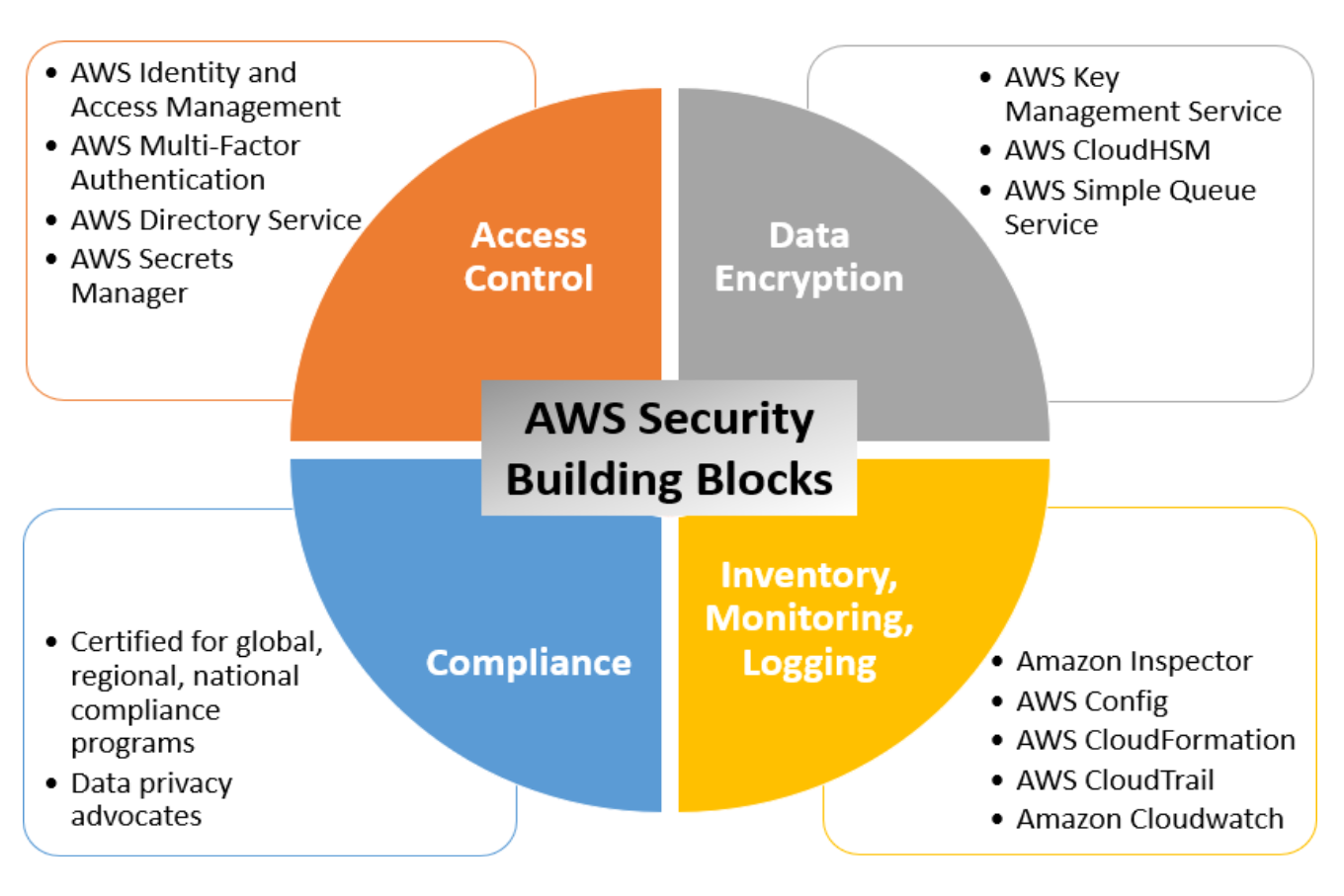
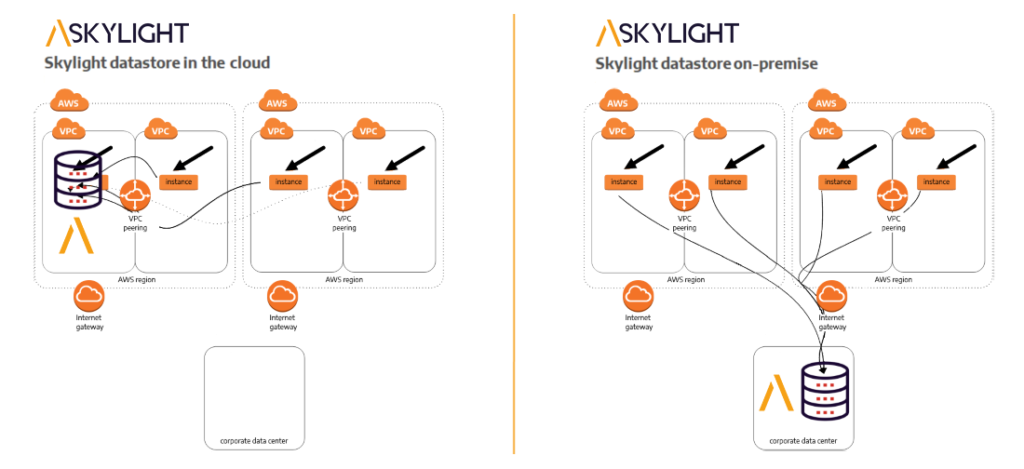
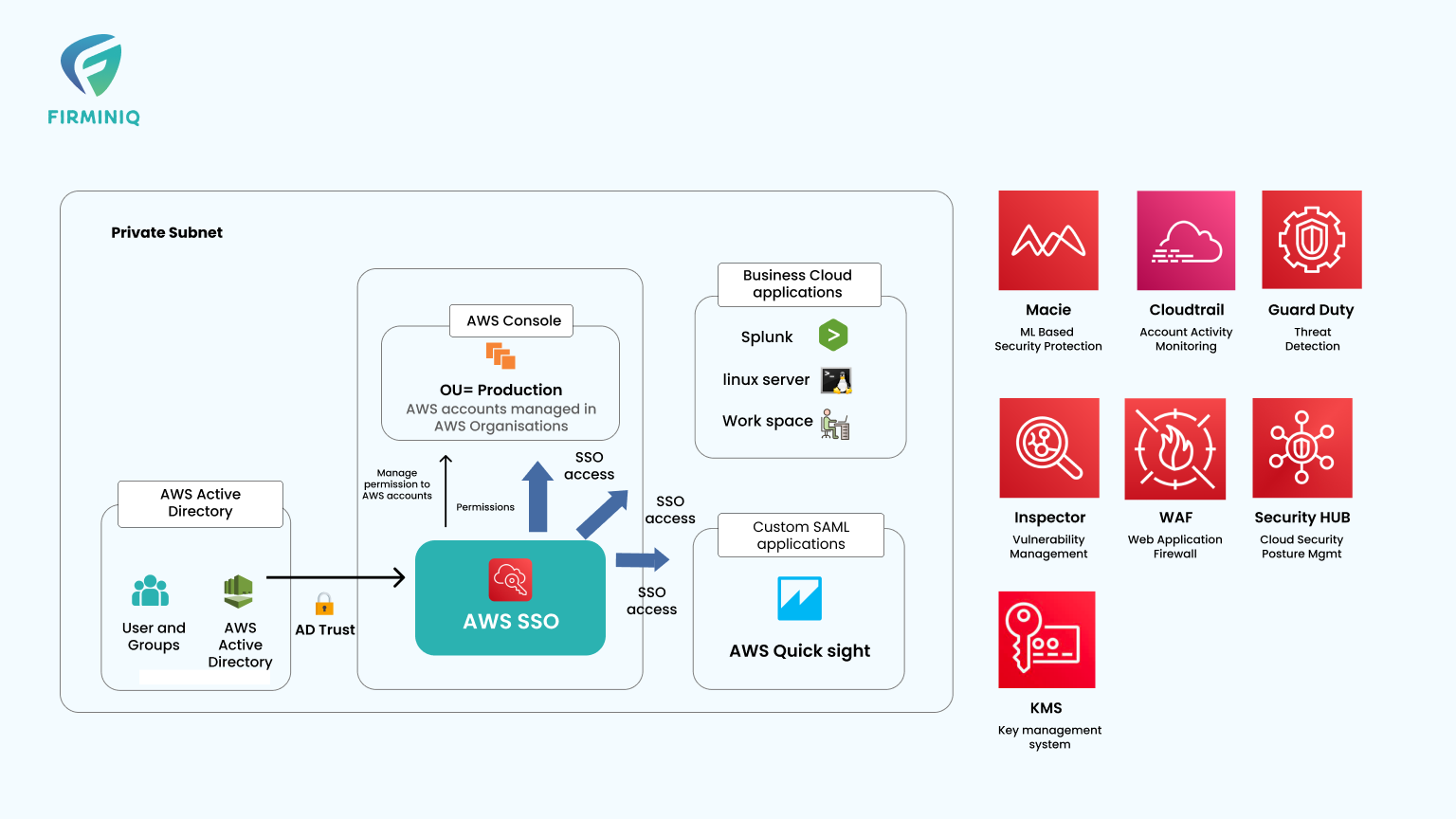
Automate security orchestration in AWS Security Hub with Trend Micro Cloud One | AWS Public Sector Blog

Build a security monitoring solution with AWS AppFabric and Amazon Security Lake | Business Productivity

Continuous compliance monitoring using custom audit controls and frameworks with AWS Audit Manager | AWS Security Blog

Event-Driven Security Monitoring with Arctic Wolf and AWS Security Hub | AWS Partner Network (APN) Blog

Automating Security, Governance, and Monitoring in AWS Landing Zone to Save Time, Effort, and Cost | AWS Partner Network (APN) Blog

Collect and respond to security events: Aligning to the MovieLabs Common Security Architecture for Production (CSAP) | AWS for M&E Blog

How to Monitor Host-Based Intrusion Detection System Alerts on Amazon EC2 Instances | AWS Security Blog