OPTIMIZED PAIRWISE MASTER KEY IDENTIFIER BASED ROAMING FOR WI-FI PROTECTED ACCESS 3 SIMULTANEOUS AUTHENTICATION OF EQUALS WITH WIRELESS LOCAL AREA NETWORK CONTROLLER OR ACCESS POINT | Semantic Scholar

OPTIMIZED PAIRWISE MASTER KEY IDENTIFIER BASED ROAMING FOR WI-FI PROTECTED ACCESS 3 SIMULTANEOUS AUTHENTICATION OF EQUALS WITH WIRELESS LOCAL AREA NETWORK CONTROLLER OR ACCESS POINT | Semantic Scholar

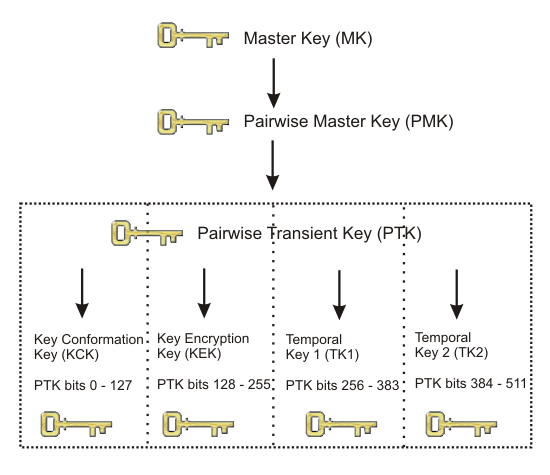
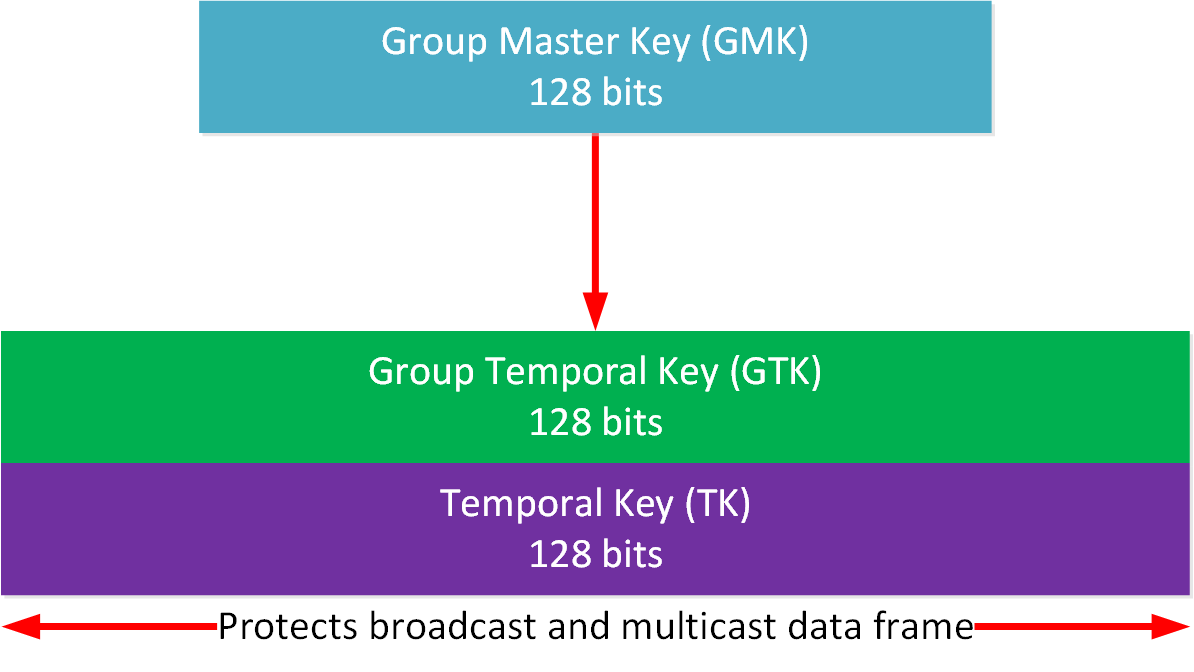
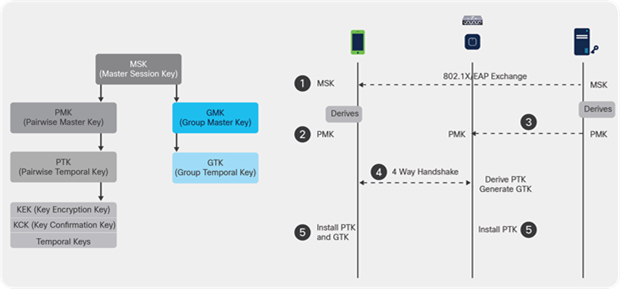
Addressing the WLAN Security Challenges > Cisco Unified Wireless LAN Security Fundamentals | Cisco Press

OPTIMIZED PAIRWISE MASTER KEY IDENTIFIER BASED ROAMING FOR WI-FI PROTECTED ACCESS 3 SIMULTANEOUS AUTHENTICATION OF EQUALS WITH WIRELESS LOCAL AREA NETWORK CONTROLLER OR ACCESS POINT | Semantic Scholar
OPTIMIZED PAIRWISE MASTER KEY IDENTIFIER BASED ROAMING FOR WI-FI PROTECTED ACCESS 3 SIMULTANEOUS AUTHENTICATION OF EQUALS WITH W

What Should I Know About New Hacking Attacks Against Pairwise Master Key Identifier (PMKID)? - PNJ Technology Partners, Inc.

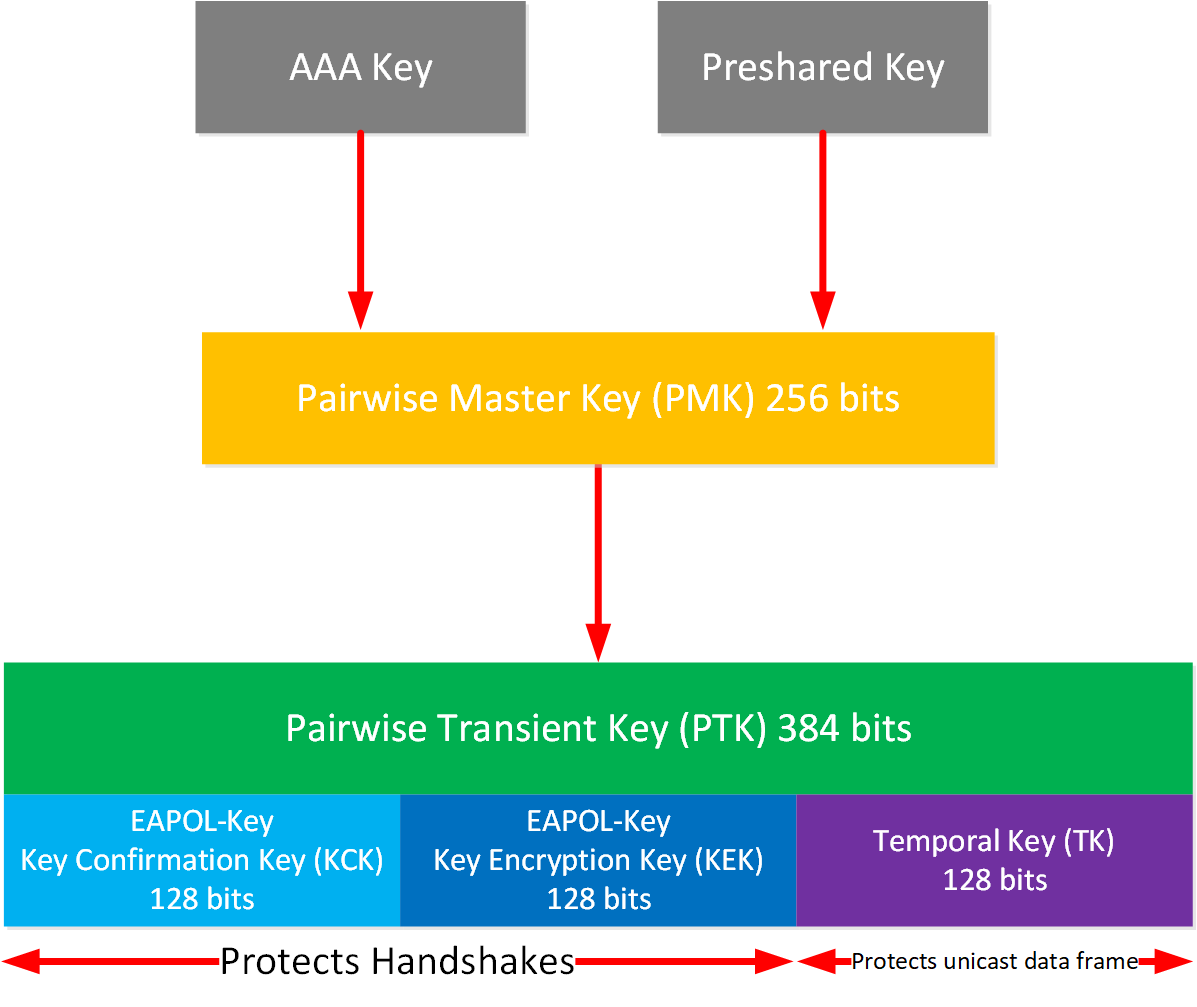


![802.11 Network Security Fundamentals [Cisco Secure Services Client] - Cisco Systems 802.11 Network Security Fundamentals [Cisco Secure Services Client] - Cisco Systems](https://www.cisco.com/en/US/i/200001-300000/200001-210000/203001-204000/203835.jpg)